Yup, it happened.
Hackers have been able to hack TV sets. The guy behind the hack called himself, The Hacker Giraffe, and managed to exploit a Google Chromecast vulnerability in devices and posted a privacy warning (and promoted PewDiePie, a YouTube celeb).
According to Media Post, the hack takes advantage of router settings that make smart devices viewable on the public internet. This includes Chromecast streaming players. Hackers can user this backdoor into connected TV sets and push videos.
That’s what The Hacker Giraffe did and left an odd message on sets: “ATTENTION: Your Chromecast/smart TV is exposed to the public internet and is exposing sensitive information about you! To find out more about what to do and how to fix this, visit [ WEBSITE NAME ] for more information.”
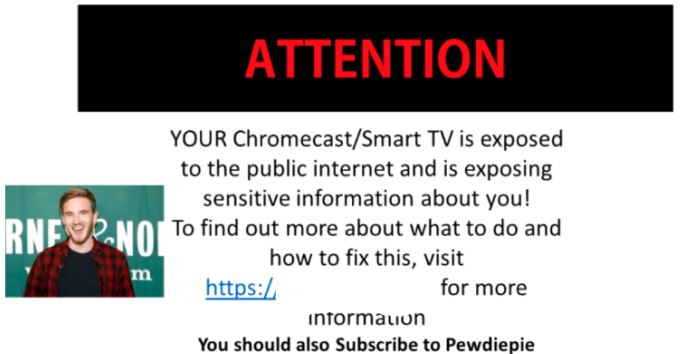
Image Courtesy: TubeFilter
Because it’s the internet, after all, one of the links to “fix” your device was a Rick-Roll, taking you to a video of Rick Astley’s Never Gonna Give You Up.
Going to the website now gets you this warning message…
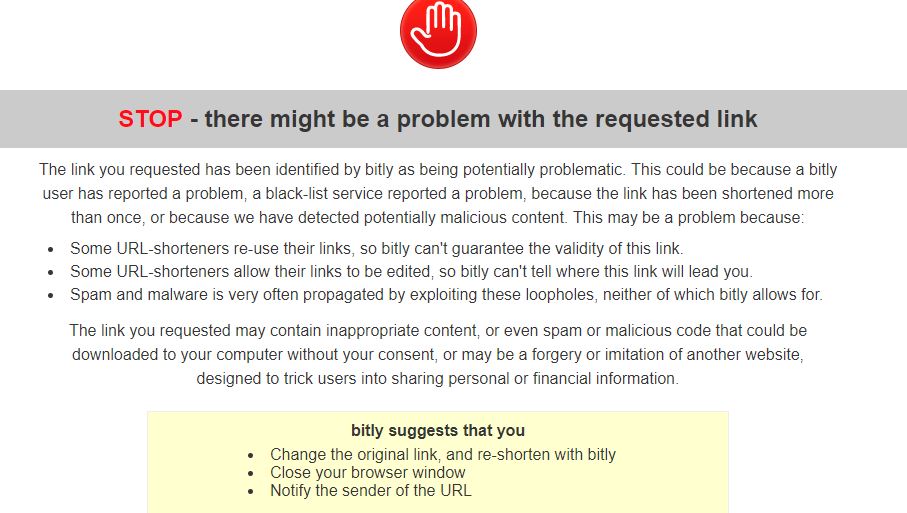
… I grabbed the info before it was stopped. Here’s what was posted…
72,341
Current Target:
Total renamed devices
8,254
Total devices forced to play video
65,283
Total Google Homes devices
1,542
Total SmartTVs/Chromecast devices
67,049
FAQ – Frequently Asked Questions
What is going on?
If you came here because you’re a victim of #CastHack, then know that your Chromecast/SmartTV/GoogleHome is exposed to the public internet, and is leaking sensitive information related to your device and home.
What information is being leaked?
What WIFI your Chromecast/Google Home is connected to, bluetooth devices it has paired to, how long it’s been on, what WiFi networks your device remembers, what alarms you have set, and much more.
What can hackers do with this?
Remotely play media on your device, rename your device, factory reset or reboot the device, force it to forget all wifi networks, force it to pair to a new bluetooth speaker/wifi point, and so on.
What CAN’T hackers do with this?
Assuming the Chromecast/Google Home is the only problem you have, hackers CANNOT access other devices on the network or sniff information besides WIFI points and Bluetooth devices. They also don’t have access to your personal Google account, nor the Google Home’s microphone. They do have access to the noise level in the room though 🙂
Who are you?
Your friendly neighbourhood @HackerGiraffe and @j3ws3r. We just want to have a bit of fun while educating and protecting people from open devices on the internet. We were also behind the #PrinterHack and #PrinterHack2.
Why are you doing this?
We want to help you, and also our favorite YouTubers (mostly PewDiePie). We’re only trying to protect you and inform you of this before someone takes real advantage of it. Imagine the consequences of having access to the information above.
What do you want?
Well, fix your device first. Also subscribe to PewDiePie on YouTube! Also Pyrocynical, Dolan Dark and grandayy. Don’t forget good ol’ Keemstar!
How do I fix my device?
Disable UPnP on your router, and if you’re port forwarding ports 8008/8443/8009 then STOP forwarding them.
In a goodbye note, The Hacker Giraffe left his Twitter followers with this diatribe: before signing off.
“Yeah, I will have to disappear. Most probably for good this time. Who knows? Maybe I’ll appear in 2 weeks on this same account again. No matter how much I write, I can’t describe to you the mental stress and panic I’m going through right now. But I won’t complain about that, because people will say I brought this on myself, I did those “hacks”, I deserve the consequences. But I’m a human too, don’t just throw away all my emotions because of my “hacker” personality. I don’t deserve to be thrown under a bus for wanting to help people, but I guess that will put a smile on some people’s faces.
But I will say this. There are still so many devices exposed to the public internet. Routers with default passwords, telnet servers with bruteforcable passwords, open UPnP servers (GOD D*** UPNP WILL BE THE DEATH OF US ALL), open SMB printers, freaking LGTV/Samsung/Sony TVs, so forth and so forth. I had a huge list of next targets, some even with ready PoCs and code. I guess that’s all dead now.
Please secure your devices. My intentions behind this were to stop this from becoming a global outbreak, and I know many of you will not believe that such a pure intention exists, but picture your family being hacked. Would you enjoy it? Would you feel rested knowing there was something you could have done to prevent their Chromecast playing NSFW material or their printer printing infinite black pages till the toner ran out? No, I don’t think so. So I did what I believed in, what I felt like was my responsibility, and ran harmless “hacks” that would hopefully alert the world to fix their devices. If I’m really about to be hit with trials for what I did, then at least I know I helped the world be a little safer, and what I did will hopefully raise awareness in a lot of people’s eyes.
I cannot express the joy I felt after seeing the number of open UPnP devices go down on Shodan. Or when people were genuinely DMing me thanking me for helping them secure their office building…
